DKIM or Domain Keys Identified Mail is a method to authenticate emails. This is done in order to detect if the sender is fake or if the received email is from a forged address. Forged addresses are commonly used in phishing and email spam.
DKIM or Domain Keys Identified Mail is a method to authenticate emails. This is done in order to detect if the sender is fake or if the received email is from a forged address. Forged addresses are commonly used in phishing and email spam.
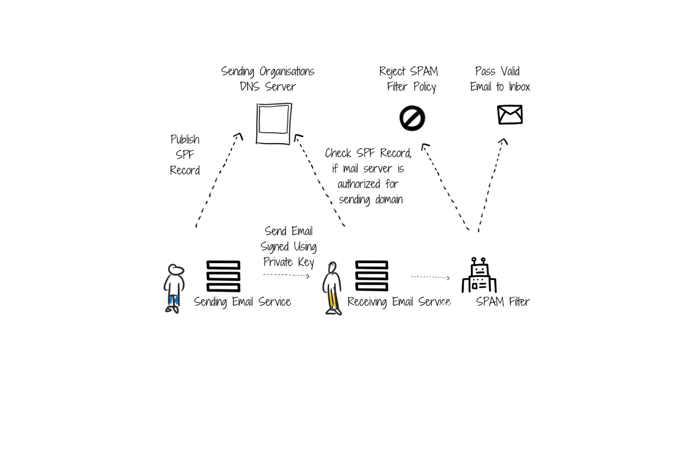 The DKIM allows the recipient to check if the email has come from the same domain it claims to be from and if the owner of that domain has actually authenticated the email. This is done using a digital signature linked to the domain name. This signature is affixed to each of the outgoing emails from that server.
The DKIM allows the recipient to check if the email has come from the same domain it claims to be from and if the owner of that domain has actually authenticated the email. This is done using a digital signature linked to the domain name. This signature is affixed to each of the outgoing emails from that server.
Here is an example of a DKIM signature:
A DKIM signature is recorded as an RFC2822 header field for the signed message.
Example:
DKIM-Signature a=rsa-sha1; q=dns;
d=example.com;
i=user@eng.example.com;
s=jun2005.eng; c=relaxed/simple;
t=1117574938; x=1118006938;
h=from:to:subject:date;
b=dzdVyOfAKCdLXdJOc9G2q8LoXSlEniSb
av+yuU4zGeeruD00lszZVoG4ZHRNiYzR
In some cases, the signature also comes with a guarantee concerning the attachments in the email. It guarantees that the attachments have not been modified after the signature was attached. This is an effective way to safeguard against malware spreading through emails. In most cases, the DKIM is not visible to the recipient or the sender– all the verification and the checking is carried out automatically by the infrastructure itself.
It is especially easy to spoof an official email ID. Fraudsters fool susceptible recipients by claiming that they are from reputed organisations in order to make them read and interact with the email they send. This can be prevented using DKIM since the signature affixed to the email is verified for authenticity.